Welcome to the important news site.
What comes to your mind when you hear the term “security gap”? That a bunch of dangerous hackers sit behind their computers and look for users’ passwords?
Or maybe you think that a young man in his twenties is sitting in his house and without seeing the color of the sun, he is constantly hacking different people. If you think that passwords are hacked or hackers’ personalities are such things, we must say that you are completely wrong.
Such things do not happen in the real world. Rather, the only reason for the occurrence of such issues, basically comes back to us and the simple passwords of our user accounts. If the passwords of the user accounts fall into the hands of one person, the work is over.
If your password is short and simple, you’re done. However, these passwords have low security and are much easier to hack than you think. This is where you have to pay attention while coding. All our digital assets today are summarized in these user accounts.
Therefore, maintaining and protecting the passwords of user accounts is of great importance. Because if these passwords fall into the hands of unreliable people, it is not clear what problems you will face.
On the other hand, some methods of hacking passwords are much easier than you think. Danger is always lurking and one must be prepared to deal with it. For this reason, we will continue to introduce 7 of these ways and methods and tell you how to deal with them.
1) dictionary attack
The first and most common method of hacking passwords is a dictionary attack. In this method, hackers examine almost all the words and get help from them one by one to reach the user’s password. Maybe this is the reason why this attack method is called a dictionary.
Of course, the meaning of dictionary is not the same books that we used in school. Rather, this dictionary is actually a very small file that includes all the combinations most used by users.
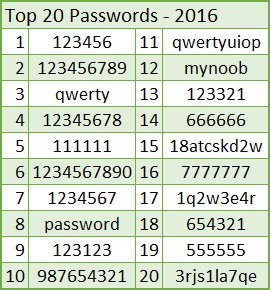
Passwords like: 123456, qwerty, password, mynoob, princess, baseball and other frequent combinations like this. The positive point of this method is that it is very fast and can be used to hack many passwords.
But the problem is that it has limited ability and cannot handle complex combinations. Therefore, it is possible to deal with this method by setting complex passwords. In addition, it is suggested not to use the same password, especially on multiple accounts.
Because in this case, when a user account is hacked, the hacker’s access to all your other services and accounts is opened. If you have a forgetfulness problem and cannot remember several different passwords, it is better to use password management apps.
2) pervasive search attack
The second hacking method that we should mention is the comprehensive search attack, in which the hacker examines and tests all possible scenarios to reach the final combination of the password. Even in this method, all the technical specifications and complexities of passwords are taken into account.
Somehow the hacker has to use anything to get your password; From the use of lowercase and uppercase letters to the name of the restaurant from which you order pizza. Hackers who often work with this method generally start with popular combinations that use letters of the alphabet or numbers.
For example, 1q2w3e4r5t, zxcvbnm, and qwertyuiop are the first combinations hackers look at to get a password. In theory, this method will eventually work. Because in the end, the hacker has to consider all possible possibilities.
But considering the complexity and number of characters of each password, using this method can keep the hacker busy for a long time. Therefore, it is recommended to use symbols and small and capital letters when choosing passwords.
3) Phishing
Phishing is not considered as a password hacking method. But when you fall into the trap of such issues, you will not have a happy ending. In this way, an email is sent to billions of users around the world. But the problem is that these e-mails were not sent by God’s will, and a breathtaking trap is hidden behind them.
Principally, phishing is done in this way:
1) First, by sending a fake email that talks about the goals of a large organization or a new business, it identifies the user as a target.
2) Most of these emails are labeled as urgent and very important and ask the user to immediately refer to the link in the email to get more information.
3) By clicking on the link in the email, the user enters a fake login page, which is basically a fake version of the website of the original organization or business.
4) After providing personal information, the user is referred to another page where there is almost nothing special.
5) Finally, the user’s personal information is stolen or sold in the most cruel way and becomes a tool for extortion.
Unfortunately, the growth of phishing is also increasing day by day, and more personal information is being stolen every day.
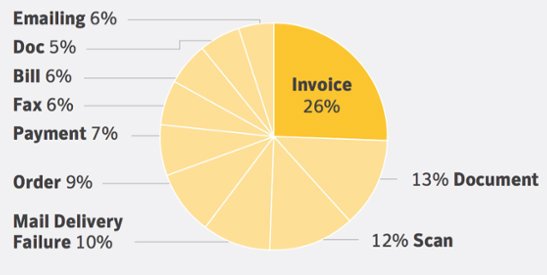
According to the Symantec 2107 report, currently fake invoices are the main phishing method to deceive users.
However, spam is easily detected by email service filters. You just need to put more filters to better identify spams to prevent hackers from accessing your information to a large extent.
Also, you can use link checkers, before entering anonymous links, make sure of their health and reliability.
4) Social engineering
One of the most dangerous types of attacks is social engineering. In this way, the hacker can access all the user’s personal information without pressing a single key. But what is social engineering and how does it work?
All the services we use these days include a support section. Often in these sections, users’ problems are dealt with and their questions are properly answered.
The important point is that all these service providers use specific phone numbers that are completely identifiable. However, not all people pay attention to this issue and thus fall into the trap of hackers.
The phone rings and the user is told that the office of the company whose services you are using has moved to another place and for this purpose we have called another number. Then, for various reasons, they ask the user for the desired service information or password.
The interesting thing is that this method is successful in most cases and the user provides the desired information to the profit seekers without any doubt. Of course, social engineering attacks are not always that simple.
A hacker can come in with different methods and trap even the smartest people. But what should be done against such threats? Perhaps this type of attack is the only case that the user alone cannot stand against.
Minimizing these types of threats depends on training and security awareness. Therefore, it is the duty of the government and the media to make people aware of how such attacks are formed.
5) rainbow table
Rainbow table is basically a kind of offline attack to get passwords. For example, hackers get a list of their usernames and passwords, all of which are encrypted.
All this encrypted information is also hashed. This means that the appearance of this information is very different from the original password. For example, if your password is “logmein”, the MD5 hashed version of it will be something like “8f4047e3233b39e4444e1aef240e80aa”.
Isn’t it strange? But in most cases, hackers have access to hashing algorithms, and through them, they compare a list of text passwords with a file of encrypted login passwords.
However, hackers don’t do this in a traditional way, and instead of looking at millions of different possibilities, they use a rainbow table.
Rainbow Table is full of special pre-defined hashing algorithms that minimize the number of possibilities. The good thing about using this method is that you can hack countless complex and difficult passwords in a short time.
But on the other hand, using rainbow tables requires having enough space. Each algorithm has its own rainbow table. For this reason, one should have countless rainbow tables in order to get help from them in the right circumstances.
However, dealing with rainbow table attacks is not a simple task. You should pay more attention to the sites. Therefore, it is better not to go to sites that use MD5 or SHA1 algorithms to hash passwords.
In addition, using sites that require you to provide short and simple passwords is also not a good idea. For this reason, it is better, besides considering safe passwords, pay attention to the sites you use.
6) malware or keyloggers
Malware is almost everywhere. But their excessive growth also brings many problems, one of which is the disclosure of user input information. Especially if a person’s system is infected with malware that contains a key logger, security loses its meaning and all his user accounts are at risk.
In addition to these malwares, they can directly touch the user’s personal information and use a Trojan to take control of the system and steal all of them. But on the way of malware, there is always a big barrier that is not so easy to cross.
Powerful antiviruses can completely solve these problems and quarantine or destroy all malware on the system. So, to prevent cyber abuses, it is better to install a powerful and lightweight antivirus on the system before any problems occur.
7) Spidering
If a hacker targets a specific organization or business, they will likely try a series of passwords associated with that business. However, the hacker can collect a series of related phrases and make his way through it.
You may have heard the term “spider” before. These spidery searches are very similar to those that index all content. Then the word found is used to open the accounts, the advantages of which can be mentioned the easier hacking of user accounts with a high degree of importance. But on the other hand, if the security of that organization is strong, such a way is not an answer at all.
We suggest you to visit the content of Windows, Office and Android
We hope you enjoyed this Training, what do you think about this post?